Beyond Walls and Guards: The Blueprint for Modern Data Center Security
.avif)
As our world generates more data than ever before, the challenge of physically securing the data centers that store it has become increasingly complex. Traditional security measures, including thick walls, vigilant guards, and basic cameras, while still necessary, are no longer sufficient. The modern threat landscape demands a smarter, more adaptive approach.
The core challenge is clear: how do you protect these critical facilities, inside and out, against threats that range from simple tailgating to sophisticated, state-sponsored attacks? The answer lies in building intelligent layers of defense that scale with operational complexity, moving from a reactive posture to a proactive, predictive one.
This is the modern blueprint for data center security.
From Manual Oversight to Automated Intelligent Defense
The foundational elements of data center security, such as perimeter intrusion prevention, multi-factor access controls, and comprehensive surveillance, remain constant in their purpose. What has changed is how these elements must operate.
For smaller or lower-tier facilities, manual oversight and rigid, labor-driven playbooks have often been the default. But that model cracks under the pressure of scale. Hyperscale and advanced colocation data centers cannot rely on human operators to manually sift through thousands of alerts and camera feeds. The sheer volume of data makes it impossible.
As our CTO, Vikesh Khanna, recently expressed in an interview, “Higher-tier or hyperscale data centers have begun shifting to agentic systems – security infrastructure capable of ingesting massive volumes of video, access, and sensor data, and autonomously recognizing threat patterns,”
Instead of just recording events, these systems understand context. This isn't about replacing guards with more cameras; it's about augmenting human expertise with intelligent decision engines that can identify risks in real-time. Building this AI-first foundation is the most effective way to scale security alongside your operations.
When Security Systems Learn to See

The flood of raw data from cameras and sensors has made human-reliant monitoring obsolete. The game-changer is AI that doesn't just see, but understands.
Modern AI-powered physical security platforms leverage behavioral analytics to flag intent, not just presence. This adds a critical layer of context that transforms security operations.
Consider the difference:
- Legacy System: Alerts on a propped-open door. Is it a technician unloading equipment or an intruder? An operator has to investigate, wasting valuable time.
- AI-Powered System: A camera sees the propped door, but the AI system also identifies the delivery truck, the person in a company vest, and the scheduled work order. It correctly classifies the event as a low-risk, routine activity. Conversely, it can spot an individual loitering near a secure fence line at 2 AM with no corresponding authorization and immediately escalate it as a high-priority threat.
This is the shift from manual triage to machine-led orchestration. By focusing operator attention on validated, context-rich events, AI turns a reactive security operations center (SOC) into a proactive command center.
Balancing Security with Operational Efficiency
In multi-tenant colocation environments, the need for robust security can often feel at odds with the need for smooth, low-friction operations. How do you secure a facility with hundreds of tenants and vendors coming and going every day without creating bottlenecks?
The answer is not to choose one over the other, but to use intelligent systems to achieve both. Take tailgating, one of the most common and easily missed physical security breaches. A simple door sensor can't tell if two people followed one badge swipe.
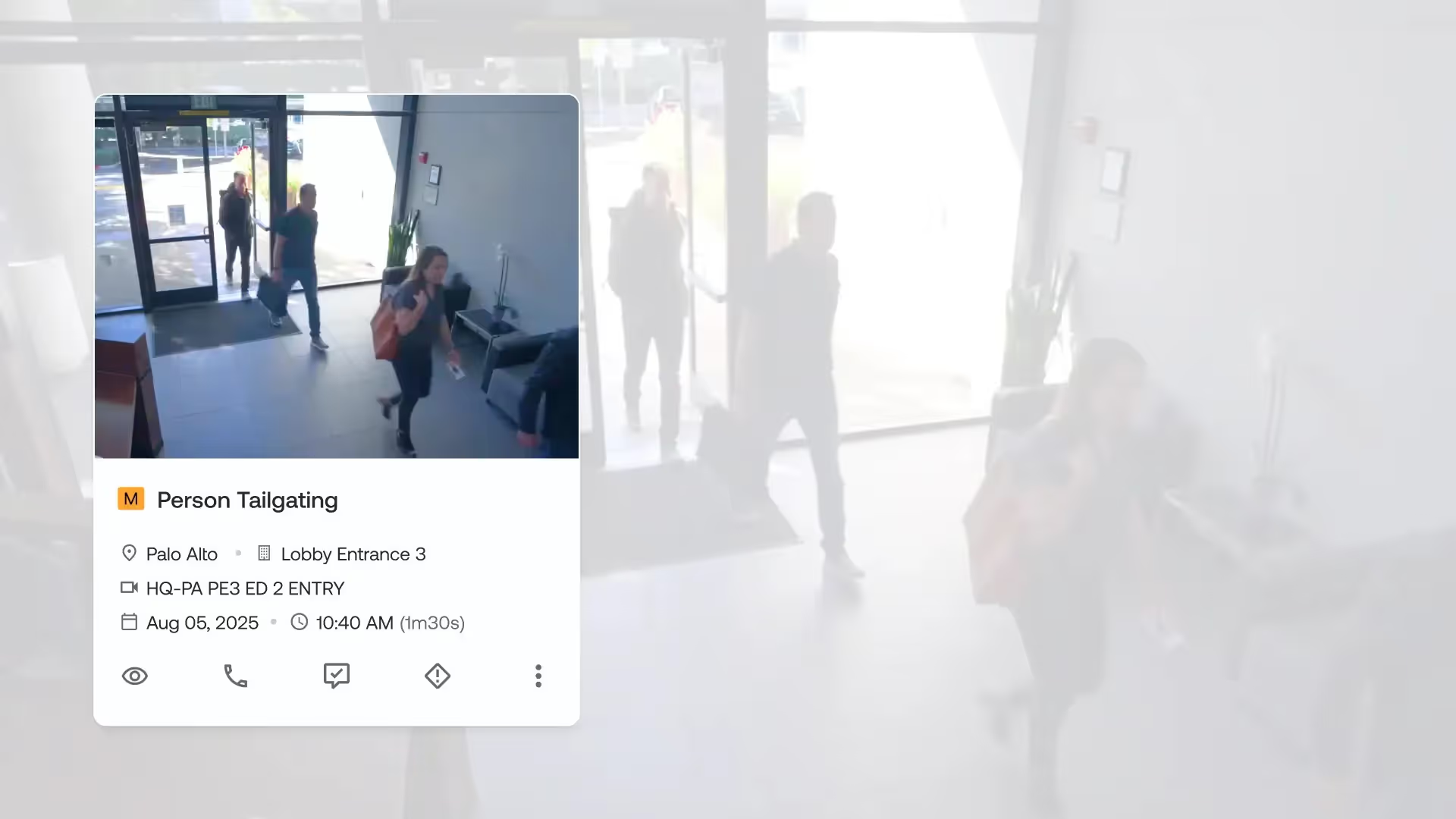
AI-powered access control validation can. By defining clear policies, for instance, "one badge read, one person enters" in high-security zones, operators can use AI-powered video analytics to enforce them. The system can visually verify every entry event, automatically flagging tailgating or pass-back attempts without requiring a guard at every door. This is a prime example of how context-driven AI enables both high security assurance and low-friction operations.
Mitigating the Insider Threat
Industry reports consistently show that a significant portion of data breaches involve an insider, whether their intent is malicious, negligent, or simply accidental.
Mitigating this complex threat requires moving beyond simple permissions and integrating physical security with logical and cybersecurity systems. The first step is to define your critical assets: specific server rows, secure labs, or network closets. From there, AI-powered systems can monitor not just who enters an area, but how they interact with those assets.
Imagine an employee who logs into a server remotely from a suspicious IP address. Your SIEM (Security Information and Event Management) system flags it. An integrated physical security platform can automatically correlate that digital alert with the physical world. Within seconds, you can:
- Use their badge ID to pull access logs and see their last known location.
- Review the associated camera footage to see if they were actually at their desk or if someone else was at their terminal.
- Trace their physical path through the facility to see which server racks they interacted with, helping to dramatically reduce incident response time and mitigate potential impact.
Securing Edge and Modular Deployments
As computing moves to the edge, security must follow. Modular and remote data centers present a unique challenge: they often have no full-time staff, no local SOC, and no immediate backup.
This is where autonomous security becomes essential. Smart operators are deploying intelligent video analytics at remote data centers, creating a "minimally viable SOC" that relies on machine-led enforcement. These systems can analyze events locally, differentiate between a raccoon and a person cutting a fence, and escalate only verified, high-risk events to a remote command center.
Edge security is the ultimate pressure test of a modern security model. It proves the need for systems that know when to act, not just when to notify.
Advancing Physical Security Towards Intelligent and Integrated
The forces shaping the data center industry, like hyperscale growth, geopolitical shifts, and the rise of the edge, are the same forces redefining its security. The old model of siloed systems and reactive monitoring is giving way to an integrated, AI-first approach. By building a foundation of intelligent surveillance, contextual access control, and autonomous threat recognition, operators can build data centers that are not only more secure but also more efficient and resilient.



